First, we should define what phishing actually is. This is a type of phishing attack on the Internet in which attackers attempt to obtain sensitive information from the user, such as passwords, credit cards, and banking information.
The attack usually starts with a fraudulent email that looks like an official communication from a trusted source (bank, online store or other company). This e-mail may contain links to fake websites that look like the operator's original site to get users to enter their credentials or other sensitive information.
If a user provides their sensitive information on a fake website, attackers can use it to steal money, commit fraud or other identity crimes.
A phishing attack doesn't just have to come via email. There are more types of phishing. For example:
- Vishing: Unsolicited calls (Sample here)
- Smishing: Unsolicited text messages
- Spam on social networks
How to recognize an attack
There are several ways to recognize a phishing attack:
- Check the sender's address: Check that the email is really from the company or person it says it is. Fraudulent emails may have strikingly similar sender addresses, but have errors in them that could indicate they are fraudulent.
- Check the links: If you find links in the email, check them carefully to make sure they lead to real websites. Try hovering over the link without clicking it to see where the link takes you.
- Be wary of urgent requests: Phishing emails often contain urgent requests, such as changing a password or verifying an account, to get users to quickly provide their sensitive information. This is one of the most common options.
- Check grammar and spelling: Fraudulent emails often contain errors in grammar and spelling, so it's a good idea to note any imperfections.
- Be cautious if the email is not about you: If you receive an email that at first glance has nothing to do with you, it may be suspicious. Be careful as this could be a phishing email trying to get your sensitive information just by replying.
- Use antivirus software: Use antivirus software and a firewall to help protect your computer from hacking and other similar threats.
Instructions on how to prevent phishing and cyberattacks in general were prepared for you by Lukáš in the previous article The user's cyber security ten.

Example of a phishing email
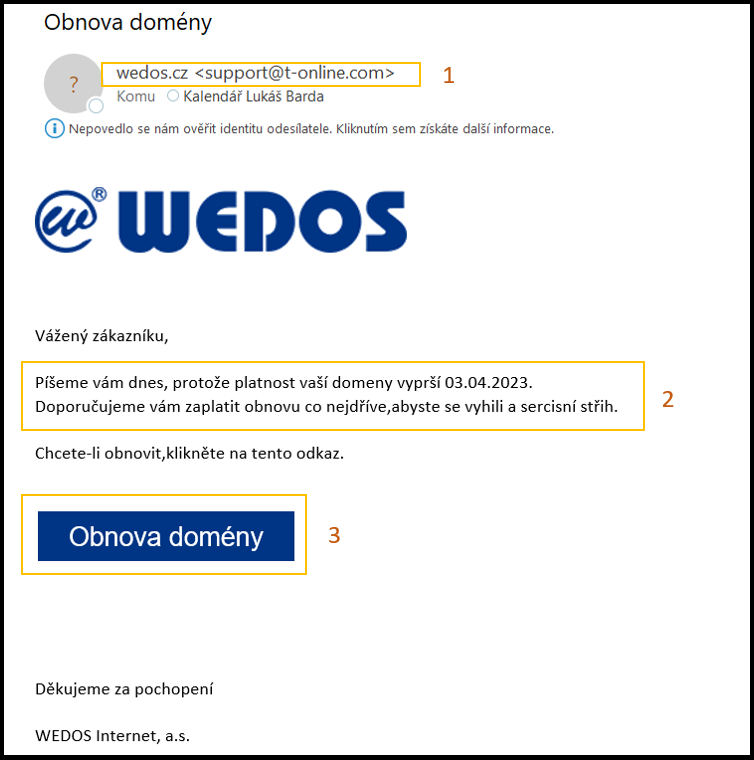
After receiving a similar email, I stop, think and follow the steps in the previous paragraph.
- Wedos probably won't communicate with me from the address support@t-online.com. (#1 in the picture)
- Link Domain renewal leads to a strange address - I can find it by hovering the mouse without clicking. Again, there is nothing similar in the address wedos.cz (#3 in the picture)
- The email contains pressure: Something will stop working for me if I don't react quickly. (#2 in the picture)
- To avoid a sercis cut? That they don't know Czech in Wedos? Probably hard. (#2 in the picture)
- This email is about me, but that doesn't mean it's not a scam.
- My antivirus program filters out a lot of other messages that don't even get to me and I don't need to pay attention to them. And thanks for that.
Remember that most attacks are automated and untargeted. Emails are sent out by the thousands by an automatic machine. It's not about you specifically, and people reassure themselves that they're not interesting and that it can't happen to them. But every device and every person is important and interesting for an attack. Phishing is like fishing. You cast and wait to see who catches. And the fisherman also doesn't care if he catches Pepa or Tomáš.
How to proceed when reporting
If you believe you have been a victim, you should report it as soon as possible. You can most often contact:
- Banks: If this is a hack targeting your bank details, you should contact your bank immediately and inform them.
- Companies: If the attack targets a specific company, you should contact that company and inform them of the situation.
- Organs: Contact the police or another organization that deals with cybercrime. You can fill out the association form here CZ.NIC, which cooperates with the police of the Czech Republic.
- Email service providers: If you have received a suspicious email, you can report it to your email provider. Most providers have mechanisms for reporting spam and similar suspicious messages.
- Reporting to databases: There are also various databases that collect attack information and warn users. You can try to report the attack to these databases such as Anti-Phishing Working Group.
If you decide to report a phishing attack, you should try to provide as much information as possible about the attack, such as the sender's email addresses, the URLs that redirected you, and how you were harmed. This information can help in the investigation of the attack and can also help other users to identify similar attacks in the future.



